




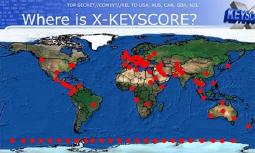
The Big Leak
As we all know, everything we do on the internet is collected by various organizations and used to create detailed profiles on individuals and their interests, fetishes, beliefs, etc. Let's imagine a hypothetical scenario where all these detailed profiles on people leak - how would the world change? How many governments would fall apart as officials are exposed? How many people would be forced to hide in obscurity as they're found to hold beliefs or do things that society does not approve of? Would society learn to forgive past digital transgressions?
Opennic and Cyberpunk DNS
What happend to opennic ? It was a /g/ concieved project. Its still functional. There are dnscrypt public servers. There is even a .cyb tld. Why are there no .cyb sites? Go make some blogs or something. Someone point arisuchan.cyb here.
Cyberpunk Lasertag
Me and my fren have dreamed for years about constructing an immersive cyberpunk themed combat arena for airsoft and lasertag! with grimy streets, bucket loads of neon and a gripping plot!!! We're starting to make this a reality, we need to show this a viable business venture! We have a crowdfunder to raise money for building a prototype of the custom guns, as well as looking into VR and augmented reality!! Please consider supporting us or sharing with your friends, it would be greatly appreciated!! Heres our media handles, please consider supporting us!
/cyb/security meetup
So the general meeting time will be around UTC 4:00 Friday / Saturday, which converts to 9 PDT, 10 MDT, 11 CDT, and 12 EDT across the United States. Convert this to your local time if you're outside of the US.
Matrix
I thought we could use a Matrix/Riot thread.

Gab Dissenter
>Gab Dissenter (or simply Dissenter) is a social news aggregation and discussion service. Dissenter was created to allow commenting on any Web page in an associated third-party forum outside of the site owner's control. The platform includes a website and a browser extension.

cyber PUNK?
Anyone notice how theres alot of talk of cyber, but not alot about punk on here?
Security on Mobile Devices
There's a lot you can install on computers to keep yourself safe against tracking/stay anonymous/keep privacy, but what about on phones/other mobile devices? Applications protecting against tracking and whatnot are much more limited.


Onion homepage
http://lain666n2yf5gnqgxk3uyqlceyt77uqcyjga5iz7owkildqlfezhypad.onion/

Earning Coins
What are some /cyb/ ways of making money/earning a living? Working at Shlomo's zaibatsu isn't very enticing. At the moment I'm scraping by making websites for people. I think the most cyberpunk way of making money is probably selling drugs online but prison doesn't seem that good so I haven't delved into it. So how are we earning our shekels arisu?

BSD for beginners
I am a Windows person, because I have to do heavily Windows oriented programming. I know linux-fu, but I don't like the distro environment where there is so much bullsoykaf going on. I want a security & privacy oriented, no-bullsoykaf, stable approach. That's why I have "Switch to OpenBSD" on my to-do list. Like I said I know linux-fu (gnu coreutils, basic configuration) but I don't know detailed configuration, I still need to look up stuff time to time.
Creating/hosting an Email Server
Hello,
cyber room
Why are you not using tox yet /cyb/? P2P encrypted text, voice, video, and group chat. Full support for tor if you want anonymity. This kills the discord botnet. We have an lain dedicated room setup there. Keep it comfy no racism allowed..
Israel, a future cyberpunk state?
Israel population is expected to double by 2050 to 16 million people and the country will be seriously overcrowded. More than 100 skyscrapers were built in the last 10 years and over 200 others are under construction. The country is the second most militarised country after Singapore. Israel is very highly educated but is faced with extreme inequalities and is one of the most diverse in the world (less than half speak Hebrew as their mother tongue, the country has the highest percentage of its population fluent in three or more languages). It's economy is based on high tech (cybersecurity, biomedical engineering, aerospace engineering, solar power…), military exports, and is controlled by a few megacorps with cyberpunk names like TEVA Pharmaceutical Industries Ltd., ELBIT Systems Ltd., DELEK Group Ltd., ORMAT Technologies Inc., OPKO Health Inc., etc. The culture is very punk: no respect for authority even in the army and workplace, a "no future" attitude… The economy is expected to grow until the GDP per capita is the same as in the United State, but with vastly greater inequalities. The country faces very serious security challenges, including from Hezbollah, Hamas, Syria, and Iran. Finally, the general aesthetics is pretty cyberpunk. The pic is an 18-year-old Christian girl, military police officer in the Israel Defense Forces.
Service Discovery
http://185.10.68.195/opencensysdir/extended-scans/mumble-servers64738.txt.lz4
The Internet is Fake
https://nymag.com/intelligencer/2018/12/how-much-of-the-internet-is-fake.html
looking for relaxing cyberpunk music
https://www.youtube.com/watch?v=mq3GsIQLwoI
Realtime imageboard
Realtime imageboards are the future. They solve traditional imageboard's ease of exit barrier. chen2.org launched as a test run that got too popular, hitting 4chan level ppd on accident.
/cyb/ + /sec/ - Cyberpunk General
/cyb/erpunk:
Anonymity General
In an effort to appease moderation I've decided to speak up about something I've been meaning to ask for a few months.
Russia possibly making its own intranet
https://futurism.com/russia-cut-off-internet-bill-law
Secure modem thread
I have a problem going on for long now. Basically: my ISP is a bitch

Encrypted Synchronous Communications (Instant Messengers)
lets talk about instant encrypted synchronous communication lain. what are some you use? which ones would you never use? should you trust your life on any of them? p2p or decentralized? how do "chat bots" fit into all of this? where do we draw the line between anonymity and convenience? how do we deal with metadata?
Database exchange
Please note that we have proceeded to the databank exchange.
SSTVNet?
SSTV is an amateur technology that permits drawing images from sounds. [File is an example of SSTV.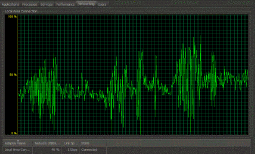
Windows 7 hardening
hello /cyb/,

Australian ISPs ban "bad" websites.
Each day we find ourselves creeping towards the corporate dystopia we fear.
Eyes Under Big Brother
Facial recognition is being employed by the government and soon to commercial use as a means to keeping tabs on everyone doing everything. Storing that data for legal uses, selling, and enforcing law.
BBS in Asia
Bulletin Board System are still popular in China/Taiwan and have millions of users.
Retroshare
Retroshare is a p2p program providing email, chat rooms, file sharing, forums, channels, over fully encrypted tunnels. It can replace most things you need to do online. Find it at http://retroshare.net/ or through your distributions package manager. Retroshare has gotten many new features recently.

Hacking General,
What are you hacking, cracking, bypassing?
VirtualBox E1000 Guest-to-Host Escape
https://github.com/MorteNoir1/virtualbox_e1000_0day
35c3 - ccc congress
idk whether this chan is even still alive, but it was a year ago, and if anyone is coming to leipzig this year, there's more lain fanatics to be met. Come to the fuwa beria assembly.
Archery OS
This is a relatively new fork of Arch that I learned about that purports to focus on "penetration testing, privacy, digital forensics, and programming." I just wanted to ask what the rest of /cyb/ makes of it. I'm considering replacing my laptop's Arch with Archery, but I wanna know if it's what it's cracked up to be or if I should look to other distros for better implementation of pentesting tools.
Don't we do Moon Jae-in impeach protest?
Don't we do Moon Jae-in impeach protest?
KOREAN STYLE PRISON LIFE
I was hospitalized in a mental hospital soliciting room for a suspicion of hunger strike at the Seoul Detention Center. Please punish Park Sang-eun (Chairman of Presidential National Bioethics Committee) and Ham Woong (Director of Keyo Mental Hospital)
hardware tracking
what are alice's thoughts on cybersecurity from a hardware perspective?
"Cyberpunk is now"
God I hate those people.
/Fuck Facebook General/
/Fuck Facebook General/
You are not the protagonist.
We live in a cyberpunk world, and frankly, you are not the protagonist.
De-Google Yourself
It may be difficult for most and almost impossible to completely escape, but trying out best to rid ourselves of services that use us as the product is necessary to remaining as low lives.
The Federation: If You just HAVE to use Social Media
If you're currently using social networks like Facebook, Twitter, looking for a home after Google+, left social media and you're just dying to get back in please consider using a federated social network to get your message out.
Physical Pentesting
Alright /cyb/, I'm interested in becoming a physical pentester. Ive seen some interesting talks about it and it seems like an amazing job.
Sun Ultra II | retro workstations
Just got a hold of an old Sun Ultra II creator 3D workstation, with the keyboard and mouse and an extra 13w3 video card with all of the cables. Does alice know what sort of display I should get for this? It looks like there's a few Sun 13w3 monitors on ebay going for ~$300. I could use a 13w3 -> vga adapter but I kind of want a period correct monitor or at least on that matches.
File System Integrity Checking
I'm looking at deploying a server soon; I'm going to monitor the file system for any changes.
Tired
Maybe we've had this thread a million times and I'm sorry if so, but I promise I'm not trying to slide. I kind of came to this epiphany that all this anonymity and security I've spent the past half decade absorbed into is a colossal waste of time. I've never been able to convince people to use free software or encrypted communications, thus everything I work for for my own privacy is completely ruined by them. Not to mention that if anyone wanted to monitor me, they could probably get through whatever defenses I put up, Google tracks your location by using cellphone towers. I'm not perfect myself; I can't be like Stallman.
First steps to anonymity and security
Hello Lain,
Writing in patterns
When we write we produce trackable patterns. These patterns can be used to track individuals across platforms, and across identities.
What is Cyberpunk?
Cyberpunk is where science and technology meets society
Private browser
What's the best browser that respects privacy? I feel like every browser has glaring issues. Chrome is a botnet, Firefox lags on my laptop with the quantum update and waterfox has terrible performance. I've been using Iridium which is a modified version of Chrome for privacy, but there haven't been any updates so I think the project is dead like ungoogled chromium, which is more or less the same thing.



The Scene
I have always been curious about the scene and the topsites.
Cyberpunk Game
Gentlemen,
Fare avoidance/Mifare cracking
!SANDBOX THE PDF!
Hacking Conference Stream
Watching a stream from HOPE in Manhattan. Figured I'd share it. Does anyone have any favorite gamedesign/penetration testing/ software talk videos they want to recommend?
I'd like to try my hand at hacking my college.
Greetings, so in the first year our Networks teacher told us that if we could pull off a hacking stunt on their network he would reward us greatly. What could I learn, search and apply practically in order to gain some better knowledge on netsec and hacking? What specs should I know from their network, to take advantage?
/cyb/ Police Stories
Ever had any run ins with the po-po in your life? I'll start.
Black Out Plan
In the past we have seen governments blocking WhatsApp, DNS, or even IPFS like in Spain just recently. Now, imagine there are protests in your country right now and your brilliant leader decides to go full retard. Do you have a plan in case things go down? One you can reach without working internet? You cannot google things if google is unreachable. We should think about this before it happens.

Like /z/ (remember /z/?) but cyberpunk
I don't know Spanish but after a quick machine translation it seems it's themed around Nick Land.

Kioptrix lvl 1
Anyone here pentest?
Spy vs Counterspy
this thread should be a place for all the spooky things.
Google Chrome - Botnet?
Hey Alice,

stuff against social networks
So me and a friend (hi miek if you're out there) are going to do a course in his school about the evilness of social networks, their habit to fuck you in the ass when it comes to privacy and the fact they are a filthy instrument of da Capital to control the masses.
Mesh Networking and File Sharing
What's Alice's experience with mesh networking and file sharing technology? I hvae been considering trying to make a network of Raspberry Pis that host access points to a single mesh network, primarily for file upload and retrieval that allows for propagation of files to the other nodes on the network.
Which means of communication for direct action?
Ok so, let's say there is a group of people wanting to squat places and similar stuff, there is a secure way to communicate other than irl?
Startpage vs Duckduckgo
Used to search with DDG, now use Startpage because it comes with a proxy option. Basically, when you connect to a site using the proxy option, Startpage retrieves the site and shows it for you, so your IP is never revealed to the site, and the proxy extends to other links you click on. Pages take longer to load and some things break because JavaScript is blocked, but I think that's a reasonable price to pay for anonymity.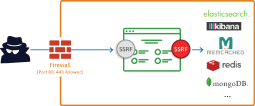
WebAppSec Lesson: SSRF
Hi Alice,

Last vpn thread, I swear.
Does anyone have or can link me to something that makes a .gif of the robot guy in GitS typing really fast?
Wearable Computing
Wearable computing is the study or practice of inventing, designing, building, or using miniature body-borne computational and sensory devices. Wearable computers may be worn under, over, or in clothing, or may also be themselves clothes
Neuralink Singularity
https://waitbutwhy.com/2017/04/neuralink.html
/Unauthorized Access General/
/Unauthorized Access General/
Palantir Using New Orleans to Test Predictive Policing Technology
http://archive.is/iQJB2
Looking for temporary /cyb/security lead.
I'm not sure when I'm bringing back the Friday night /cyb/security meetup. If anyone would like to pick it up for me, go ahead. I've been really busy as of late with school and I'm horrible with time management, so Fridays and the weekend end up being for things I procrastinated on.
Advanced Intel
Does anyone have any information on this store: http://www.advanced-intelligence.com/other.html
Synthetical Science
Synthetical Science is one of the first networks of network researchers that emerged in 2010. This group of nettalkers was looking for hidden files in the secret Internet segments, but the main field of Synthetical Science was "memetics," the study and creation of "mental viruses." More about memetics is written in John Ono's book "Tao of memetic engineering". The association ceased to exist in 2012.

modern day hackback tutorial?
good day lains. I was wondering about this
Keep the Future unwritten!
Ohai Lainons,
Reconfigured browser, Google doesn't work
I was reconfiguring Firefox after getting a new computer, and suddenly I can't get on Google anymore. I've checked to see that I'm accepting cookies, but I'm still unable to sign in—as in, the "Sign In" button doesn't even do anything.
[PDF] Understanding and Using C Pointers Core Techniques for Memory Management
>Improve your programming through a solid understanding of C pointers and memory management. With this practical book, you’ll learn how pointers provide the mechanism to dynamically manipulate memory, enhance support for data structures, and enable access to hardware. Author Richard Reese shows you how to use pointers with arrays, strings, structures, and functions, using memory models throughout the book.

MIT 6.858 Computer Systems Security, Fall 2014
>6.858 Computer Systems Security is a class about the design and implementation of secure computer systems. Lectures cover threat models, attacks that compromise security, and techniques for achieving security, based on recent research papers. Topics include operating system (OS) security, capabilities, information flow control, language security, network protocols, hardware security, and security in web applications.
tox chat
Tox is a decentralized encrypted alternative to skype developed by chan users for chan users. It supports text, audio, video, and group chats.
Trouble #8: Hack the System
Hey Arisu, do you watch Trouble? It's a monthly show made by submedia, the same guys who used to make stimulator's ITEOTWAWKIAIFF. Unlike that show Trouble is not about recent events but every episode is centered about a single topic.
WikiLeaks
What do you think of WikiLeaks, it seems like a good thing that helps keep people informed and helps keep tabs on governments, due one might see it as being far from separate from the agendas of governments considering WikiLeaks suppose lack of whistleblowing on Russia .

#CyberpunkMonday
Hey guys, a few of the smaller cyberpunk communities are doing a thing this year, figured you chummers might want in.
Net Neutrality
In USA they're trying to take down Net Neutrality.
The Technological Attack
I want to share some translated textes from a german collective which is working on a new social/technological critique. I´m very interested in a discussion about the toughts mentioned and how you see the future. Most interesting would be how resistance could work in a digitalized society.
Virtual Reality Spaces
There was a thread on Applechan before the wipe about making a comfy /cyb/ space for VR.
YouTube
ZeroNet

Private Internet Access is trash
Just a reminder - If you're not using thatoneprivacyguy's list as your criteria for selecting a VPN you're probably getting your info from a shill. 99% of the comparison lists on the internet are paid advertising.
Intel CSME accessed via the USB DCI interface for JTAG debugging.
https://www.reddit.com/r/linux/comments/7bmvze/game_over_someone_has_obtained_fully_functional/

Noob here. Asking for info
so i was invited here by one of the mods on discord. I know the basics of using a computer and have started avoiding using anything google related by reading threads here. Idk gow to code, change os (i can only afford a cheap acer laptop for now), or how to vpn. Any and all info would be appreciated
DHS Wants Tech to Scan Your Face as You Drive to Mexico
http://www.nextgov.com/emerging-tech/2017/11/dhs-wants-tech-scan-your-face-you-drive-mexico/142218/
Chaos Crypto
Hey Lain/Alice,
Everyday Propaganda
This was on the back of a normal milk carton here in Sweden.
DEF CON 25 YouTube Links
DEF CON 25 videos are going up on YouTube, finally.

Free speech:
A lot of people commonly conceive free speech simply as the right essentially for everyone to say one's view, in any space without restriction, that there be no private spaces.
AI Poisoning
So Lains,
CCleaner Compromised
http://archive.is/hddwi
Mark Zuckerberg 2020
>Dear Democrats, Unless You Nominate Mark Zuckerberg, Donald Trump Will Win in 2020
Politics
Why is almost anyone on arisuchan, lainchan, uboachan etc all so politically progressive?
Ropemaker E-mail Exploit
http://archive.is/DmQvU

digital suicide
I recently let go of some non-essential social media accounts to clear up my digital footprint and bamboozle the three-letter orgs a little, now I only post on anonymous boards. Then I saw the bigshot thread in /r/ and the digital suicide thing. It got me wondering. I think I will probably cut myself off the internet someday soon. I think it's only useful as a distraction and it's become something of an unhealthy habit on my part. Thoughts, agree/disagree?
merge with computers
Would you sign up for full-body cyberization if it were proven to be perfectly safe for at least 99.99% of those undergoing the procedure? Would you go even further and replace up to 97% of your brain with artificial components if you were assured that you would retain the 'neural core' of biological neurons necessary and sufficient to maintain subjective conscious experience? I'm very curious where lain would stop on the road between here and there if she would stop at all.
Making a living online
Hi Lainchan
Anyone else longing for a digital existence?
Forgive me, as I'm a tad drunk. Still doesn't detract from my point.
integrating ai to any apps
hey folks, who here had been successfully integrated a machine learning software to any apps? like open ai to any apps you like like some linux tools? hows that? and what ml library is best? ..and if you have some projects that finish, can you share it to me//? tnx folks
Tor General
Discuss News about the Onion Router, otherwise known as TOR. You can also discuss interesting .onion sites you find
/cyb/ sites
Any other /cyb/ places you guys visit? I've been visiting this site recently just because it's a bit strange. https://boards.systemspace.link/
What's with all the overly-cautious cyber-anonymity?
I've been lurking around, i see all of these articles and threads and whatnot about being like super-duper anonymous online and keeping away from all sort of data-mining or 'surveillance'. But nowhere does it explain the motivation behind it. Can you either explain this to me or link me to an explanation on why this is important?

Russia bans on VPN and Tor & surveillance
As the title says, by Nov. 1 "all software and websites related to circumventing internet filtering in Russia, including VPN software, anonymizers, and instructions on how to circumvent government website blocking" will be derezzed. On 2018 "companies registered in Russia as "organizers of information dissemination", such as online messaging applications, will not be permitted to allow unidentified users".
The future of technology
It seems like we are on the crux of a big change in the paradigm of computing; namely distribution is in vogue again. We have so many new technologies trying to be foundational infrastructure for the future, and I'm beginning to wonder what it will look like when/if these technologies mature. To name a few of the things I'm talking about there's cryptocurrencies/blockchain technology, ipfs, matrix, and urbit (to ignore all the decentralized social media platforms that have sprung up). These technologies all tackle different use cases, but all of them promote decentralization, open source, and user responsibility of data, in regards to both security and privacy. I'm not even taking into account other recent trends of AI research, the internet of things, biohacking or "actual" cyber-security, but thats an entirely different ball game.
Digital Classrooms as Data Factories
https://wrenchinthegears.com/2017/07/14/digital-classrooms-as-data-factories/
Facial Recogition: Hype Edition
Here is a .svg of the hyperface camo. I apologize this was the first time I tried something like this and I maybe screwing it up. If I did any points would be great.
Net Neutrality leave my Home alone
this whole Net Neutrality thing is really pissing me off and honestly if anything happens to it I think I might actually kill myself.
Should we welcome are A.I overlords?
Should political power be invest into machines, do Humans deserve to make there own decision's after Mankind's long history of bloody war, persecution, genocide and exploitation of others?
Why do you have a smartphone?
What is your excuse to yourself to possess and use a smartphone?

Bluesnarfing
hi /cyb/

Freeganism
pic not related.I'm not sure if this is the right place to post this but I can't reasonably post this in anywhere else.I'm reopening a discussion I've seen to some extent already.This is about sharing resources relating to freeganism.This can include guides(informative/instructive) on dumpster diving, squatting, eco friendly transport, other eco friendly lifestyle implementation and all that for ethical or personal reasons.I'll start by sharing where I found an introduction to freeganism:
Interference

Filter bubbles in brain implants
I saw this talk and it got me thinking: https://www.youtube.com/watch?v=fq7oauciBdc
HELLO CONSUMER
So amazon just went full fucking distopian: they went and got a patent to keep people from comparing prices
Backups

linux hardening
Discussion about linux hardening.

Social Engineering
Just came across this old thread in the archive and decided it needs a comeback.
Bitcoin safe wallet?
Hello,
Vault 7 General
Since there's no Wikileaks thread yet, I figured this could be a separate thread. Discuss Vault 7 & related topics (software security patches, best practices, other relevant leaks)
PROJECT X - TITANPOINTE
I thought lain would enjoy this. The whole thing is so fucking sinister. Don't get lost in the aesthetics though. The national security state is real and it has consequences.
/cyb/erpunk general
Nosebleed Edition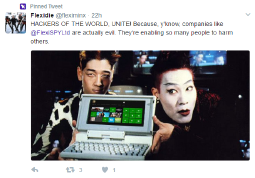
Flexispy
Looks like another one of the corporate malware makers are about to get their teeth kicked in;
/cyb/erpunk discussion
In an effort to promote more discussion of cyberpunk activities related to anonymity, privacy, security, etc. we ask that you try to make posts that are exclusively visual in nature in one of the existing threads. If you genuinely feel your post belongs in a different category, you can still make a new topic, but we are asking you to search before posting. Thank you.